Overview of the CIA Triad
The CIA Triad is made up of three principles, Confidentiality, Integrity, and Availability. Together these three tenets make up the cornerstone of network security.
Confidentiality
The confidentiality tenet is about managing permissions in a way that only exposes the appropriate data to a user/system. Ideally the minimum amount of data is exposed for the user/system to complete their task.
We can employ techniques such as data encryption, user authentication including 2FA to discourage bad actors from hijacking data that wasn’t mean for them on the system.
Failure of Confidentiality is if an unauthorised person gains access to files or systems they are not authorised to access
Integrity
The integrity tenet is about ensuring the integrity of the data on the system. We must think of many threats that may change the data, and must ensure that no data is lost.
We must protect the data in transit in a way that prevents “Man in the Middle” attacks, so a bad actor or corrupted system wouldn’t be able to change or lose the data, techniques such as encrypting files in transit, hashing and checksums to check the integrity of the files on either side.
We also must protect the data in storage as well, there can be many threats, from bad actors looking to change or destroy data, to natural disasters that can wipe out a data centre, or even drive degradation. To ensure the data isn’t lost we can employ techniques such as building redundancy into our systems and storage and keeping regular backups.
Failure of integrity occurs if an unauthorised person modifies data either in transit or in storage
Availability
The availability tenet is about ensuring the system is available to the users and systems that need to use it. If a bad actor would attack a business’ system in the form of a Denial of Service attack. Then the employees of said business may not be able to log on, access their files or their systems to complete their work. Depending on how long the system is inaccessible this could mean lots of lost revenue for a business.
Other threats such as natural disasters, power outages, software bugs, etc.
We must employ techniques with the goal of keeping a system up 24/7. With little to no downtime at all. Techniques such as employing redundancy in system components and data strategy that can protect a system from many different threats.
For example if you had a data centre in Sydney that was forced offline due to the floods. You would have built in redundancy by having a back up of that system in Perth. You may not be able to run at 100% efficiency until the Sydney centre is back online but at least you’d still be able to operate.
Failure of availability occurs if an end user is unable to access data or systems that they require
Trade-offs
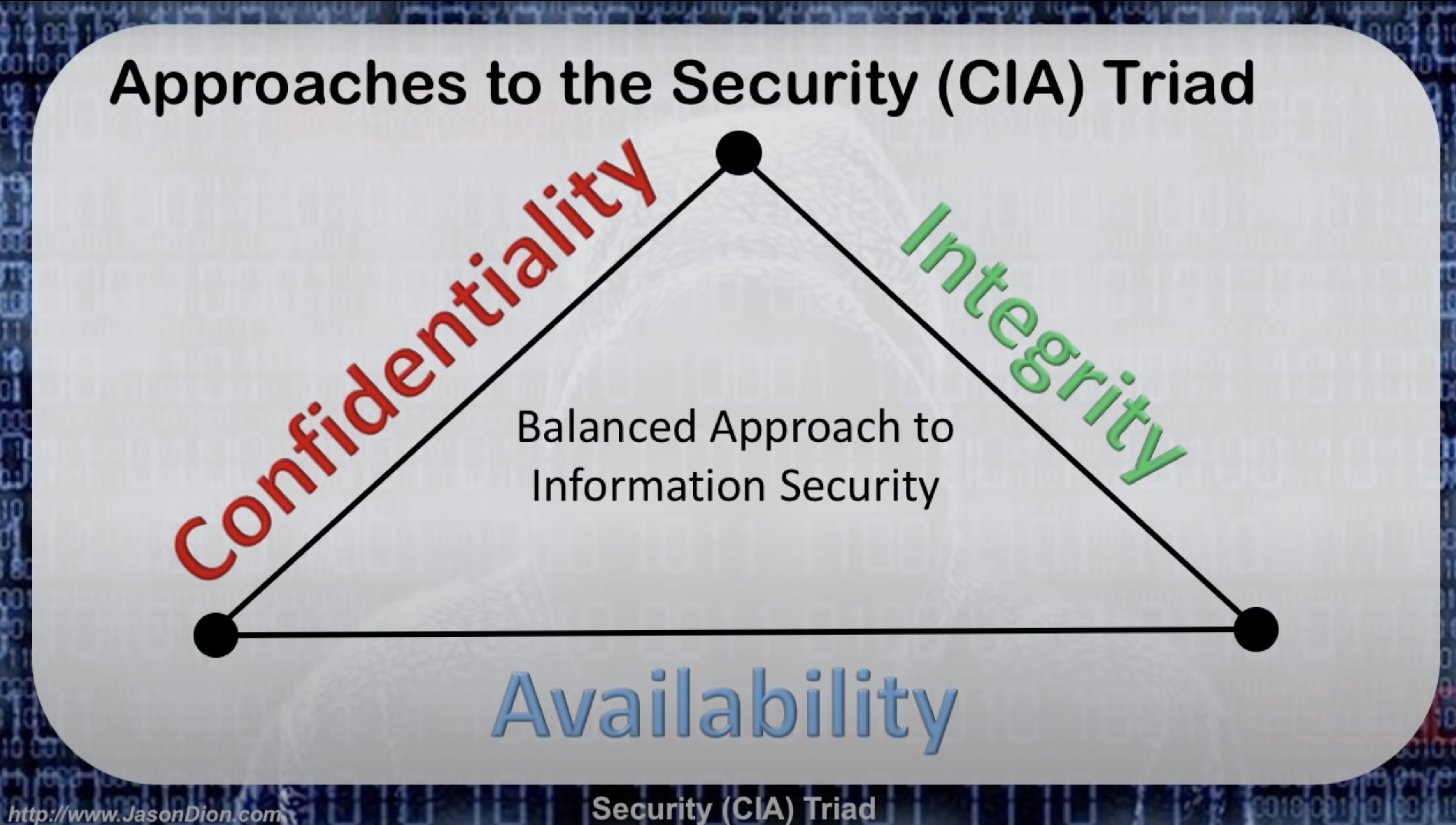
You can never achieve such a balanced approach with security of any kind. There is always trade offs because there is never enough money to have a truly balanced and impenetrable system. If someone wants to get in, the only thing you can do is keep adding friction to the process to the point where it is no longer worth it for a bad actor attempt to penetrate your system.
If a person or an organisation has the resources, money, time and willpower. They WILL get into your system.
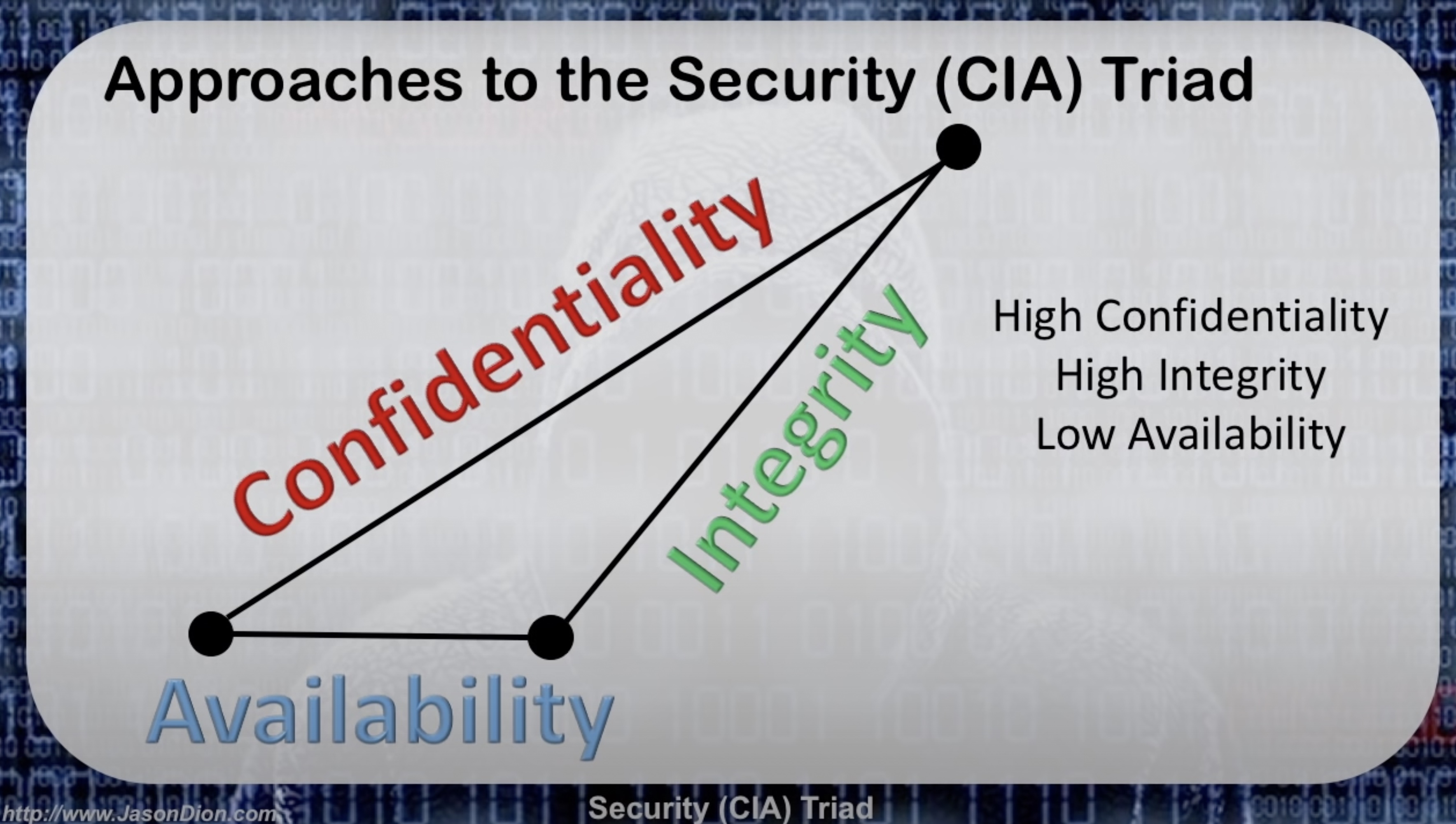
So what does a CIA Triad look like with trade-offs? The triangle above shows a High Confidentiality, High Integrity, but Low Availability.
What does this mean?
This triad would represent a system with high security measures in place but with low user accessibility, this could be anything from a file encrypted with 10 different decryption keys, to a manila folder locked in a safe in an underground bunker. Only accessible by its intended user, not easily modifiable but incredibly difficult to access should you need to.
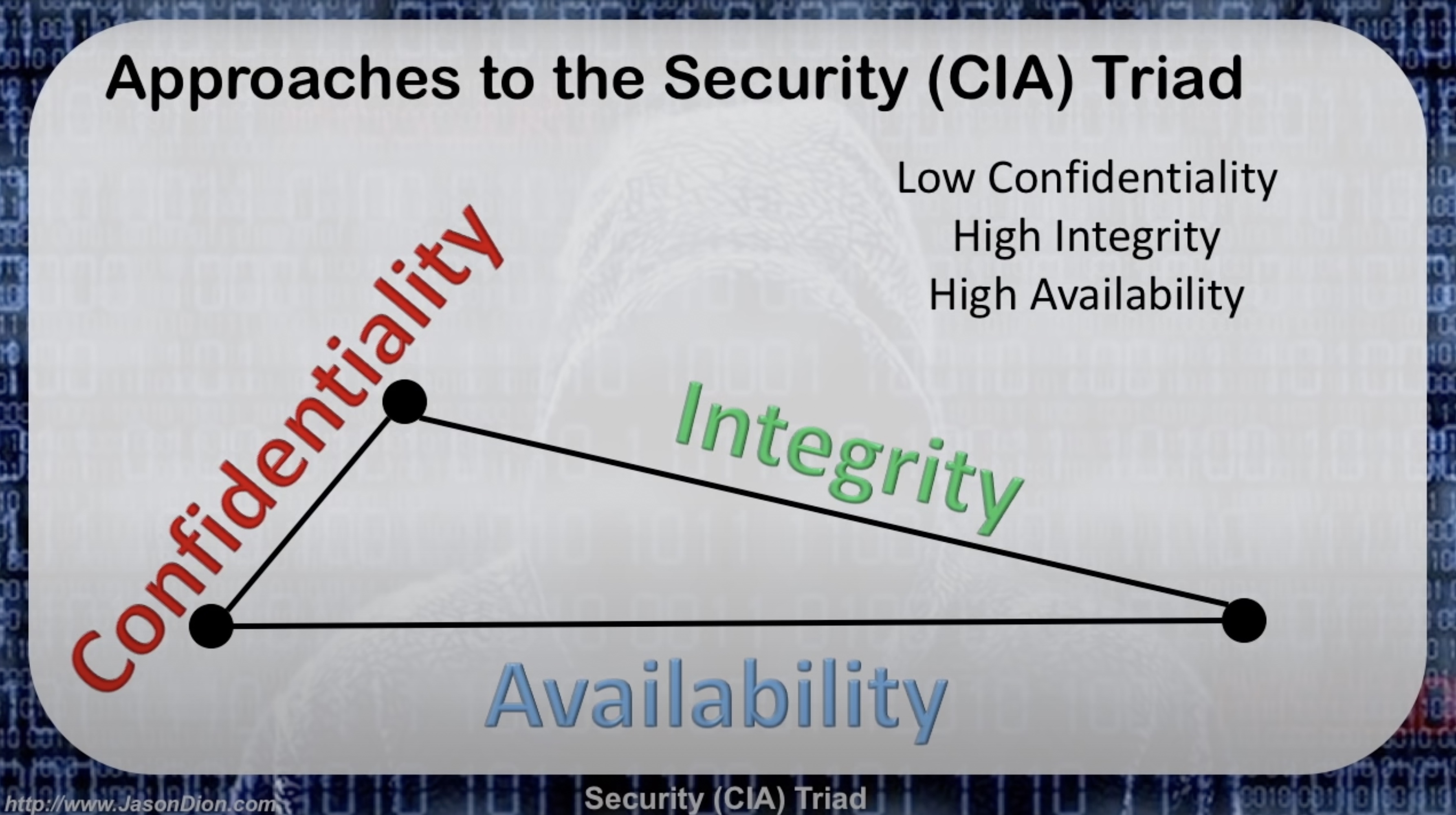
On the flip side of that we have a triad that looks like this. It shares the High Integrity of the previous triad but has Low Confidentiality and High Availability instead.
What does this mean?
An example of a system that uses this kind of triad would be a public facing website, maybe a portfolio website showing a graphics designers past projects. Data integrity would be important so it cannot be changed and always shows the authentic designs, but must also have high availability so any future employer could see their designs whenever they’d like. In this case, confidentiality wouldn’t be too important, as the intended purpose of the website is to show off the graphics designers creations. They would like anyone and everyone to have access to it.
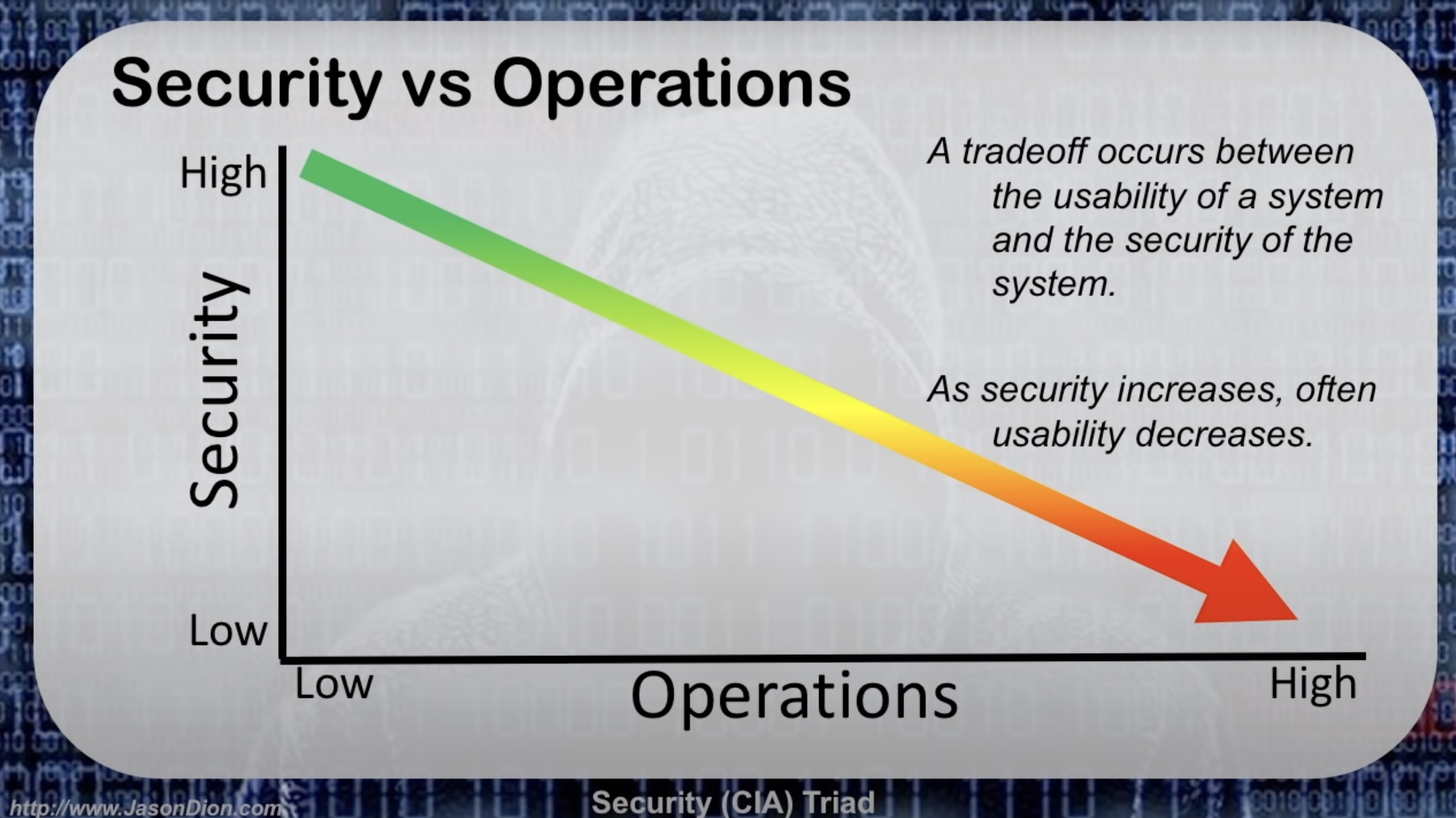
When talking about trade-offs Security vs Operations is an important part of that conversation. You can have dreams of a system that must be protected from all threats and have 100% uptime and low friction for authentication of legitimate users.
However, You cannot have it both ways, a highly secure system is more difficult to use, authentication takes longer, authentication needs to be re-check more often. There are many things of a secure system that decreases usability at the same time.
Similarly, the more usable you make a system may come with many security trade-offs in the name of convenience or productivity. Things like needing faster login processes, less authentication walls etc. But at the same time may greatly increase your risk of being hacked.
Another constraint may be money, the more you demand of the usability AND security of a system, greatly increases your cost in terms of security consulting, penetration testing and configuring of systems.
It is always a balancing act to secure your system while retaining acceptable usability with a budget that is worth the effort.